Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid. This new internet treat started being popular in 2012.
Most people are unaware of this type of threat that flows the internet on a daily basis. Security companies have been able to update their securities, but there is always someone curious enough to enter into the ransomware rabbit-hole.
There are 2 types of Ransomware:
- Locker ransomware encrypts the whole hard drive of the computer, essentially locking the user out of the entire system.
- Crypto ransomware will only encrypt specific, seemingly important files on the computer, such as word documents, PDFs and image files.
Ransomware does exactly what it sounds like – it presents users with an ultimatum: pay a fee to unlock and reclaim personal data, or don’t pay the fee and lose the data indefinitely.
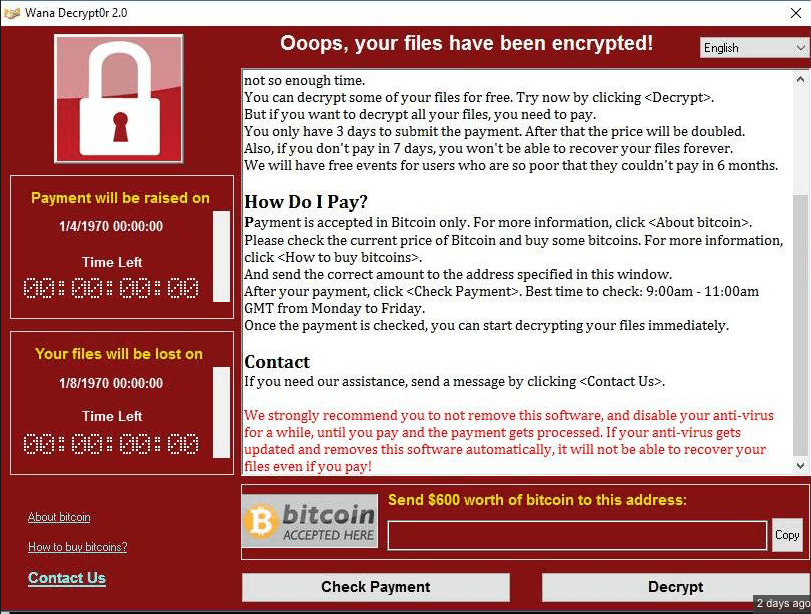
The cyber attacks by Ransomware are becoming more numerous, sophisticated, dangerous and massive, as we saw with
Since then little has changed and today the Ransomware continues to lead the world lists of cyber attacks, as the last variant of Locky spread through 23 million emails and Cerber ransomware, which in its latest version steals browser passwords and data from portfolios of Bitcoin. We recommend Carbonite as a good form of cloud data backup, they are able to store different versions of your files in case your data is compromised.
If until now the Ransomware used to have exclusively economic motivations producing high benefits for the attackers, lately it is extending objectives as a preferred method of introducing malware as we saw with the NotPetya ransomware. It is no accident that Kaspersky has put the ransomware in the spotlight in its security solutions for 2018 and that Microsoft is testing a new tool in Windows 10 against this real epidemic.
10 tips to prevent Ransomware
The typical Ransomware infects a personal computer or mobile device, blocks the operation and/or access to a part or all of the equipment by seizing the files with strong encryption and requires the user an amount of money as “ransom” to release them. We are going to provide you with our 10 best prevention tools and alternatives to prevent ransomware in your company or home office computer, but it all starts with the basic understanding of how to spot these types of attacks.
Therefore, if the best advice in cybersecurity is prevention, in the case of Ransomware it is essential to stop it. We remind you some essential tips to stop it:
- Update of the system and applications. Keeping the operating system updated with the latest security patches and all the applications that we have installed is the best starting point. The mentioned WanaCryptor took advantage of a vulnerability in Windows systems.
- The line of defense. It is convenient to install and maintain an antimalware solution, including a properly configured firewall to allow exclusive access to the necessary applications and services.
- Anti Ransom tool. It is a specific tool against this type of attacks, which will try to block the encryption process of ransomware (monitoring “honey files”). It will dump the memory of the harmful code at the moment of its execution, in which we will hopefully find the symmetric encryption key that was being used.
- Anti-spam filter. Many of the attacks by Ransomware are distributed through massive email campaigns. In addition to these filters, you should follow the general advice such as not clicking on links or opening attachments from unknown senders.
- JavaScript blockers. Applications such as Privacy Manager block the execution of any JavaScript code suspected of damaging the user’s computer. This helps minimize the chances of getting infected through web browsing.
- Security policies. Tools such as AppLocker, Cryptoprevent, or CryptoLocker Prevention Kit facilitate the establishment of policies that prevent the execution of directories commonly used by ransomware, such as App Data, Local App Data, etc.
- Accounts with privileges. Do not use accounts with administrator privileges. 86% of threats against Windows can be avoided if you use a common user instead of an administrator. That is why it is important to use a non-Administrator account for common tasks and only leave the administrator for when a series of tasks related to the manipulation of the system is going to be done.
- Showing file extensions. Showing extensions for known file types is a good practice to identify possible executable files that want to pass themselves off as another type of file. It is not uncommon to see
an .exe file with the icon of a Word document. If the extension is not visible, the user may not be able to distinguish whether it is a Word document or a malicious executable, although it is also good to remember that a Microsoft Office document can also contain malware. - Virtual machines. Employing virtual machines to isolate the main system is another effective technique. In a virtualized environment, the action of ransomware does not usually materialize.
- Backup. Backing up important data as a regular maintenance task is the most effective measure to minimize the damage in case of being infected. The backup must be hosted in an external environment different from that of the computer in order to recover the files from a “clean” site and not have to pay the “ransom” required by these cyber-criminals.